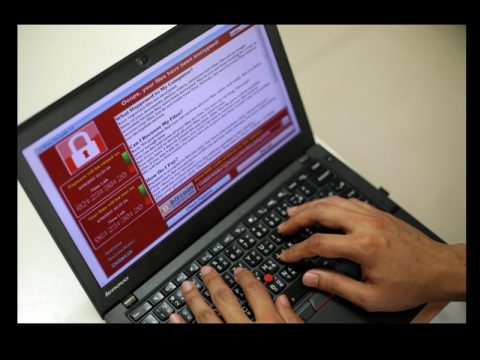
WHY THE LATEST RANSOMWARE ATTACK MAY BE HARD TO STOP
No one has claimed responsibility for a global cyberattack that disabled at least 2,000 computer systems in the U.S. and Europe Tuesday and was still spreading Wednesday morning.
Hackers crippled computers by locking up the files and demanding users pay a $300 ransom to restore access.
Ukraine reported the most attacks with its power grid, government offices, banks and grocery stores affected.
The cyberattack also impacted several U.S. companies, including the drug maker Merck, food companies Mondelez International and Nabisco as well as a Pennsylvania health care system.
CBS News senior national security analyst Fran Townsend told “CBS This Morning” that the attack, in terms of sophistication, takes the ransomware attack from this past May “to the next level.”
Though it is unclear where the attack came from, there has been speculation that Russia is involved.
“The attacks seemed to start in the Ukraine, so we know that Russia has sort of been behind these sorts of attacks against Ukraine, but I don’t think anybody really knows,” Townsend said.
Though there are similarities between May’s WannaCry ransomware and this one, known as Petya, there is a key difference.
“That was stopped because there was a kill switch. They haven’t found a kill switch to this one yet. And this is once this is out in your system, it sort of propagates itself without direct commands from the hackers, and so it is pervasive and it is sort of difficult to deal with once it’s been launched,” Townsend said.
Although the NSA has not confirmed that an NSA hacking tool known as the EternalBlue exploit was used in the attack, speculation that it was has raised questions about what the intelligence community is doing to protect the U.S. against these attacks.
“When a government creates an exploit and lets it loose in the world,, whether intentionally or not, it then gets added to and turned around like a boomerang and comes back at you. And Americans are rightly saying, ‘Wait a minute. My tax dollars helped fund the development of these tools. Don’t you have an obligation to protect me?’ And the intelligence community struggles,” she said.
Townsend thinks it’s likely that individuals will pay the ransom, but more worrisome to her is that companies may, too.
Of the companies that were targeted, Townsend said, “They lose money every day when they don’t have access to these hard drives. You know, you worry that they will [pay], which only encourages these kinds of attacks.”
As far as U.S. vulnerabilities, Townsend pointed to the failure of individuals at large organizations to install proper protection against the ransomware.
“Microsoft did what you’d expect a responsible company to do, they put what we call patches out there. So these are patches to cover the vulnerabilities in Microsoft 7 and 10, which is what the Petya attack takes advantage of. The problem is at big organizations, as you know, we have thousands of people. Is it properly installed? What we’re finding is some didn’t install it at all, some didn’t install it completely.”